Powerful endpoint security management—media protection, isolated device remote control, security diagnostics, flexible dashboards and reporting, and more—with app control and automated patch management. Detect and prevent threats before they impact you, and respond swiftly to infections. Give your team the tools they need to be immediately effective at saving your company’s data and reputation.

Endpoint Security for Endpoint Manager
Take security to the next level
Active control
Demonstrate compliance
Single vendor solution
Reduce your attack surface and improve your security posture quickly. Get integrated security including patch management, application control and reports all in one management portal.
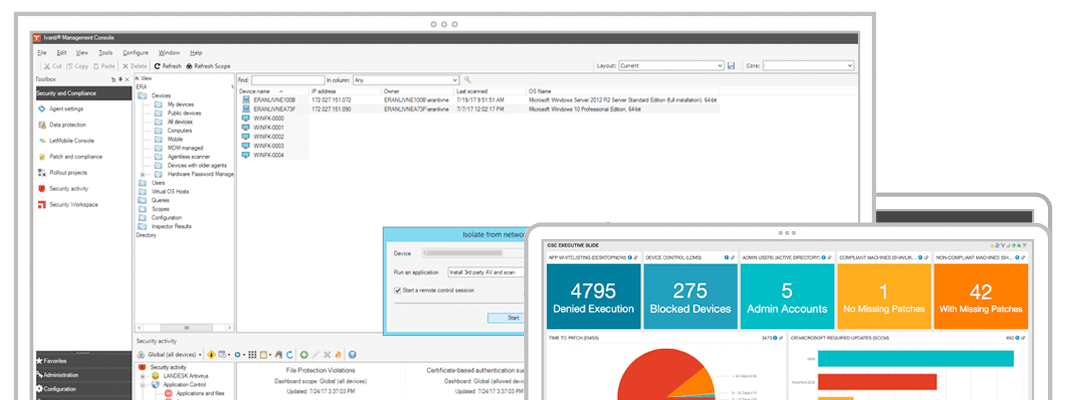
Protect your network while users do business as usual
With Ivanti Endpoint Security for Endpoint Manager, you can see everything necessary to find and remediate malware, diagnose problems and identify faulty or nonapproved processes. If ransomware invades your network, Endpoint Security will catch it, kill it, notify other connected machines and block the malware from running on them.

Discover and inventory all networked devices and software
Active and passive discovery technologies identify and inventory all IP-enabled devices in real time—even so-called “rogue” devices like wireless hubs as well as those devices behind firewalls. Automatic discovery also helps you find all the software on those devices, including usage details.

Automatically patch to ensure a stable and secure environment
Patch Windows, macOS, Linux and third-party apps across your network reliably—even those devices that are on the road, at a remote site, or asleep. Ivanti Endpoint Security for Endpoint Manager simplifies patch management, with no impact on users, through best practices, automated processes and fast deployment.

See threats. Act on them quickly. Move on with your day.
Attackers are always developing new ways into your network. Just assume you're in a state of continuous compromise and act accordingly. Get the added prevention, insights and rapid remediation you need to minimize downtime.
Auto-isolation and rapid remediation
Isolate infected device, remote control it while isolated, and remediate or reimage to protect from ransomware or malware outbreaks.
Application Control
Control which apps can run on your network. Also prevent multiple types of fileless attacks.
Device Control
Control what storage devices can connect to devices and provide logs for what is copied.
Antivirus management
Use Ivanti’s AV or choose another. Manage either from the same console. Includes dedicated ransomware protection.
Security dashboards and reports
Visualize vulnerabilities and security-related activity.
Unified and integrated
Improve security processes by managing Security, Patch, AV and Unified Endpoint Management together.
Get started
Deploy and manage proven security controls from within the console you know well.